STIR / SHAKEN PROTECTION AGAINST FRAUDULENT ROBOCALLS AND CALL SPOOFING
What is the difference between STIR and SHAKEN ?
STIR is a set of protocols enabling service providers to certify the legitimacy of the caller ID of an outbound phone with a trusted authenitcation service, which can then be verified by the terminating service provider.
What is SHAKEN?
STIR is a set of protocols enabling service providers to certify the legitimacy of the caller ID of an outbound phone with a trusted authenitcation service, which can then be verified by the terminating service provider.
Robocallers and scammers have increasingly been spoofing, or altering, their outbound caller ID to mask their identity or appear as though their call is coming from a legitimate source to deceive unsuspecting subscribers.
The Federal Communications Commission (FCC) created an industry-wide initiative to require all telecommunications service providers to incorporate a new technology standard named STIR (Secure Telephony Identity Revisited) and SHAKEN(Secure Handling of Asserted Information Using Tokens). This implementation aims to ensure that calling numbers are not spoofed, reducing fraudulent robocalls.
These spoofed calls are usually malicious attempts to sell products or services without subscriber consent, or to take money from the receiver –referred to as fraudulent robocalling.
In 2019, users in the United States experienced close to 60 billion fraudulent robocalls, causing subscribers to stop answering their phone unless the caller ID was from a reputable party. This has been destroying the trust in voice
communications, as well as the reputation of legitimate businesses trying to reach their customers..
All small service providers (over the top providers) had until June 30, 2022 to implement STIR / SHAKEN standard within their networks, in accordance with this FCC announcement.
STIR / SHAKEN CALL FLOW
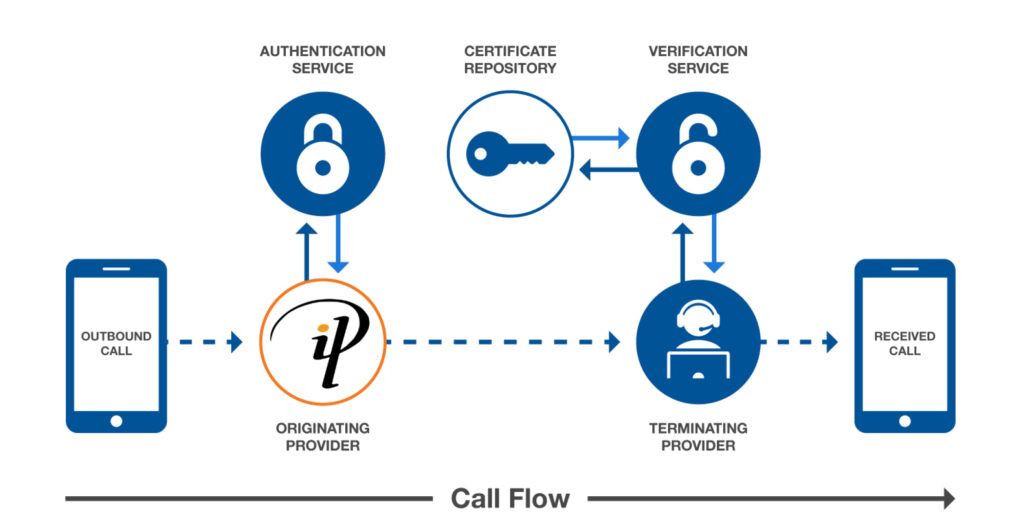
When a VoIP phone call is made, a SIP INVITE message (or call request) is created and sent to the service provider for that party, called the originating service provider (OSP). The OSP will check the source and caller ID of that call and validate it with an authentication service, which creates a digital signature, or ‘signs’ the legitimacy of the caller ID in one of 3 attestation levels (or confidence levels). The authentication service will then create an encrypted SIP IDENTITY message and sends it along with the call to the next service provider in line,until reaching its destination, and includes the following details:
- Calling number
- Called number(s)
- Current timestamp
- Attestation level
- Origination identifier
- Calling number
- Called number(s)
- Current timestamp
- Attestation level
- Origination identifier
The call then reaches the final service provider belonging to the called party, or the terminating service provider (TSP), who then verifies the SIP INVITE with a verification service. The digital signature of the OSP is obtained from the public certification repository, which is a trusted entity for STIR/SHAKEN, and verification of the caller ID is performed. The TSP decides to either complete the call or block it, based on the attestation level.
DISCOVER HOW TRUE IP SOLUTIONS CAN HELP YOUR BUSINESS WITH STIR / SHAKEN
TIPS is currently compliant with STIR/SHAKEN regulations and is interoperable with all the major carriers, which means your phone calls willnever be blocked due to improper caller ID validation and fraudulent robocalls will be minimized.
By consolidating your VoIP termination and phone number needs on TIPS’s voice network, you can assure STIR/SHAKEN compliance for your organization. All of your organization’s outbound calls over our network will be signed with full attestation, reducing the likelihood of your calls being blocked by a terminating carrier.










